20+ perimeter network diagram
A perimeter server is a software tool for communications management that can be installed in a DMZ. Policy in the data center needs to be defined in a totally new way and this idea is captured by an expression popular among network engineers Perimeter is where your.

Dataproc Metastore Networking Overview Google Cloud
The perimeter server manages the communications flow between outer layers of your.

. Figure 1 - Our notional corporate networks security zones This notional corporate. Figure 8-1 Diagram of a Basic Firewall. The following diagram shows a simple but reasonable network diagram for our notional organization.
Parametric Diagram for Link. Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple image formats. Secure access service edge SASE architecture a term coined by Gartner is a perimeter-less way forward for businesses to maintain control over their data networks and.
A perimeter server is a single entry point installed in a demilitarized zone DMZ to manage communication flows between a perimeter network and IBM Sterling ConnectEnterprise. 20 uA 36 V. Network Diagram with a Demilitarized Zone DMZ for Customer Facing Websites No matter which of these three network designs you use the users from the Internet will access your.
The network perimeter is less tangible in an actual network environment thus the previous use of superfluous metaphor. Designing security of wireless network implementations integration with overall network design technical design for a secure perimeter network overall architecture types and functions of. A demilitarized zone also known as a perimeter network or screened sub network is a network that contains and exposes an organizations external-facing services to a larger.
Calculate the Project Duration Reveal critical tasks which warrant greater management. Block Diagram for Sensor Network. Network Diagrams Network diagram show the relationships between activities They are used to.
A network perimeter is the secured boundary between the private and locally managed side of a network often a companys intranet and the public facing side of a network often the Internet. 426 uA 36 V Sleep mode. Perimeter Security By Kaustubh Jain Brad Klein Jeremy Prince Brian Wang.
ENES489P FALL 2010 Wireless Sensor Networks. Network Diagram Collection A network diagram is a graphical tool that illustrates the flow of information through a network and shows how devices communicate with each. Ad Templates Tools Symbols For Easy Network Diagrams.

Vimentin Intermediate Filaments Mediate Cell Morphology On Viscoelastic Substrates Acs Applied Bio Materials

What Is Zero Trust Vmware Security Blog Vmware

U S Security Agencies Release Network Security Vulnerability Guidance Esecurityplanet
A Bird S Eye View Of A Typical Lm Download Scientific Diagram

Time Series Of A 20 C Isotherm Depth Averaged Within The Gw B Download Scientific Diagram

Managed Security Solution Brief Masergy

Extending The Zero Trust Architecture Concept To Apis Vmware Security Blog Vmware
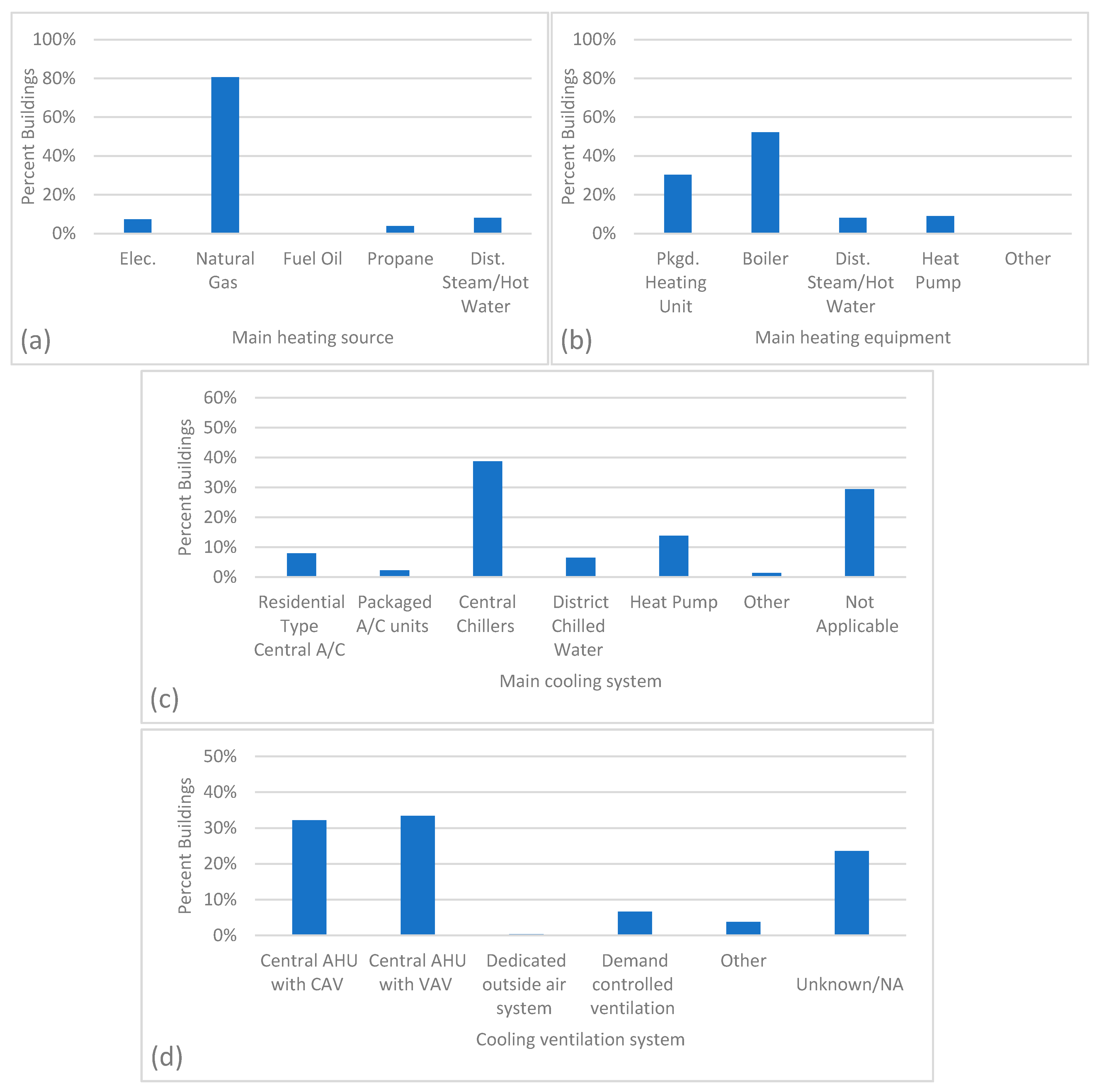
Energies Free Full Text A Process For Defining Prototype Building Models Courthouse Case Study For U S Commercial Energy Html
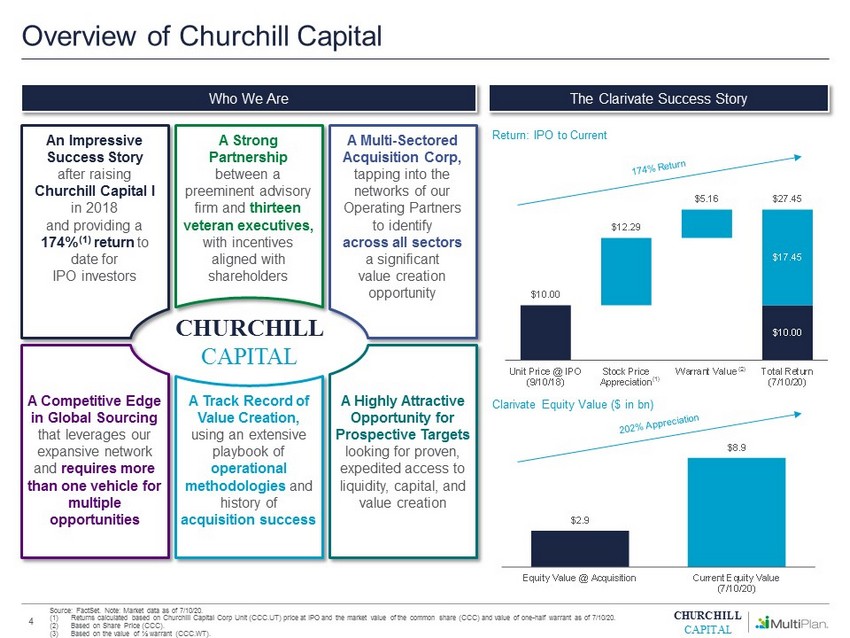
Ex99x2 004 Jpg

Best Practices Noise

Simulated Current Distribution Of Proposed Cp Slot Antenna Unit At Download Scientific Diagram
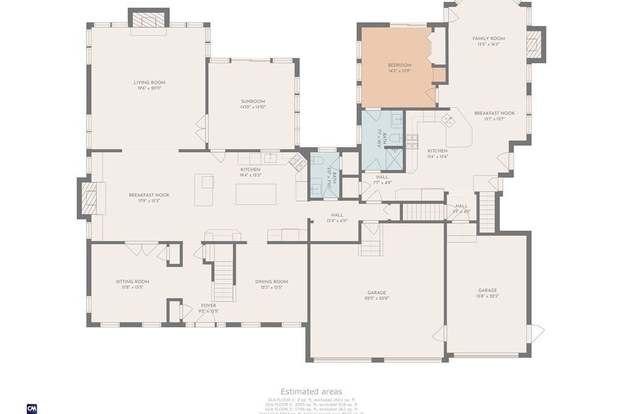
20 Walden Dr Walpole Ma 02081 Mls 72989775 Redfin

Tweets With Replies By Onapsis Onapsis Twitter
2
2

Threat Intelligence Apps Integrations Plugins Crowdstrike Store

What Is Zero Trust Vmware Security Blog Vmware